Links and guidance related to the return on mitigation report in the Microsoft Digital Defense Report - Microsoft Digital Defense Report
These statistics show the percentage of customers that have the issues highlighted and then seeks to prioritze the controls and remediation actions to give customers direction on where investment is best placed
Below are listed various links and resources for each issue and guidance to address them
If you use Entra ID, there is a lifecycle management capability that helps you manage user onboarding, offboarding and entitlement management (ensuring users only have access to what they require)
Microsoft Learn documentation showing the various ways to onboard devices
Guidance on how MDE can integrate to Microsoft Defender for Cloud ensuring cloud workloads have the MDE sensor and are integrated fully, includes onboarding guidance
A blog series from Microsoft MVP Jeffrey Appel that includes effectively onboarding devices
A guide on how to operationalize MDE with your SecOps team. Even if you use non Microsoft EDR, there are good lessons here that you can apply to whatever tooling
MDE tags devices that are publicly exposed to the internet with a specifc tag that is available in the UI and in Advanced Hunting to query on. Devices that are publicly accessible are more vulnerable to exploit and should be priortized for hardening and patching
Windows LAPS is a Windows feature that manages the local administrator account on Windows devices, to reduce the risk of credential attacks like pass-the-hash, by ensuring each device has a local admin password that is unique and regularly changed
The protect M365 guidance seeks to protect Active Directory and Microsoft Entra ID (previously Azure Active Directory) from each other in the case of compromise. If Active Directory is compromised we want to reduce the blast radius to Microsoft Entra ID and vice versa
If you use Microsoft Defender for Identity, you can use the security posture assessments to find quick wins for securing accounts and configuration
A video from Trimarc security on how to get quick security wins in Active Directory
A blog from the Microsoft Detection and Response Team on issues seen in Active Directory in real life compromises
A blog from SpecterOps covering common misconfigurations in ADCS that allow domain domination
Locksmith is a lightweight tool developed by Trimarc security that queries ADCS and can detect and remediate misconfigurations
Guidance from the NCSC about hardening Windows devices
The inventory portal can show you the status of your devices, including whether they are enrolled in MDE, the health of the sensor and any residual device risk
Guidance to block legacy authentication in Microsoft Entra Conditional Access. Although this was disabled for Exchange Online by Microsoft, it is recommended you block it using CA also as non Exchange Online services or custom apps may be using legacy auth
Both links show how to deploy Microsoft Entra ID Password Protection, a service that lets you block poor passwords both in the cloud and on-premises. Password protection works by blocking the most common bad passwords (such as Password123) and your own custom blocklist (YourCompanyName123)
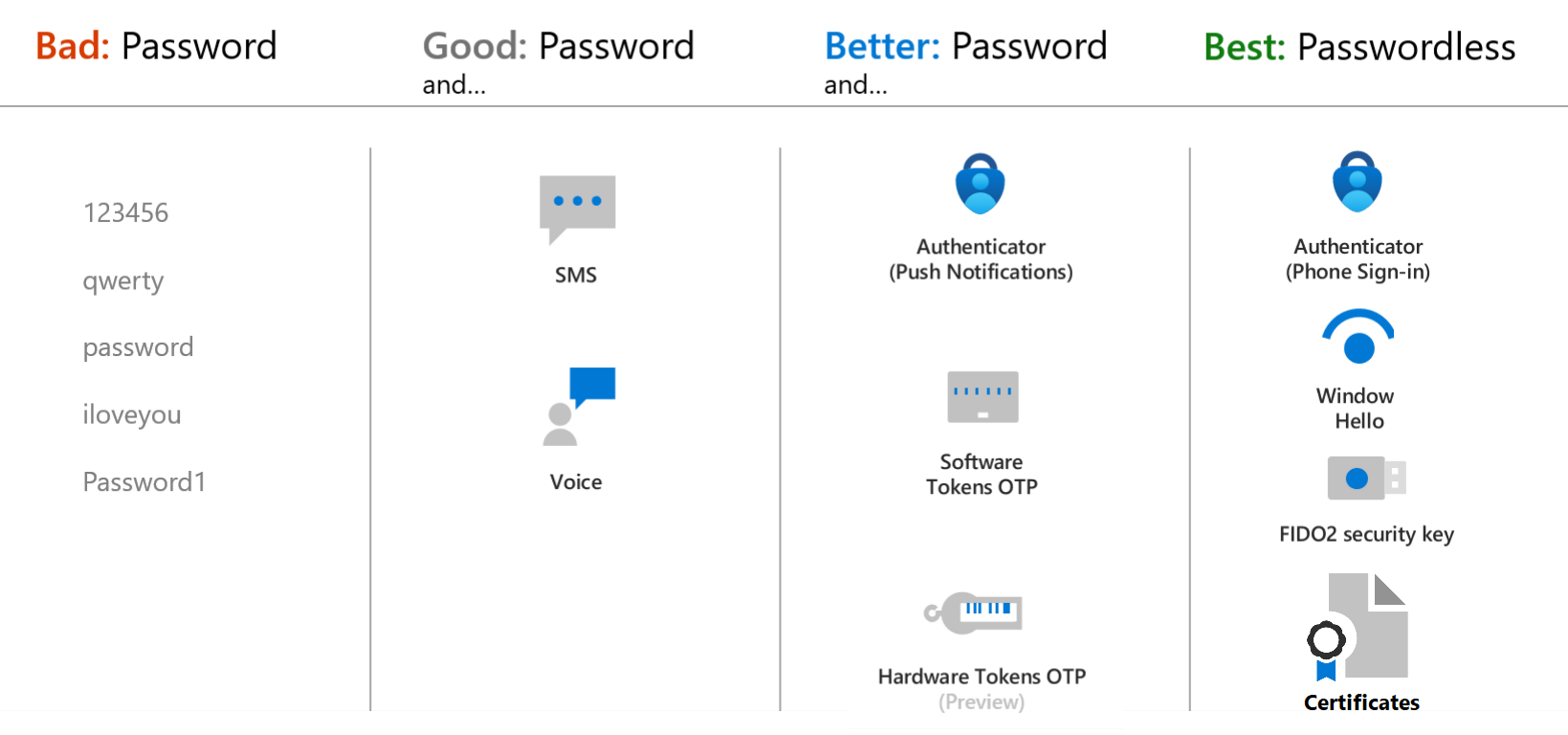
Guidance on planning your strategy from moving away from weaker MFA methods (SMS/Phone) to modern and phishing resistant methods (FIDO2/Windows Hello for Business)
This graphic is a great visual explainer
Intune device compliance rules allow you to configure policies and settings your devices must adhere to in order to be granted access via Conditional Access
Microsoft provides guidance around aligning to CIS and other benchmarks
Guidance for disabling SMB v1 and other SMB policies
Great blog from Steve Syfuhs from Microsoft about NTLM and the struggles to remove it
Managing software updates and updates to Windows via Intune
Using WSUS to update Windows
Azure Update Manager is a unified service to help govern updates across all your machines, including Windows and Linux, across Azure, on-premises and other clouds
If you are licensed for Microsoft Defender for Cloud Apps you can connect in third party apps like ServiceNow, Atlassian, AWS for visibility into those apps. They are easy to connect and build use cases for
How to use the investigation tools and interface to investigate alerts and other suspicious activity
A SecOps guide to Microsoft Entra ID including how to respond to compromise, what events to look for as a detection team and how to protect users and devices
You can use Microsoft Entra PIM to manage privileged access to your environment by requiring additional approvals or security checks to elevate to privileged roles. This access can also be time bound
If you are just starting your PIM journey you can discover your current posture to show the spread of privileged access and use that as a foundation to reduce privilege across your environment
There is an out of the box security default that will enforce MFA for privileged accounts, turn this on!
If you want to go beyond Security Defaults, there are lots of great CA templates available here
Your most privileged accounts should be using phishing resistance MFA, enable it here!
Don't just enable passwordless for your most privileged accounts, enforce the use of it with authentication strengths
SecOps guide for Microsoft Defender for Office 365 and how to respond to mail based attacks. As with all these guides, even if you use non Microsoft mail security, there is valuable guidance here
Guidance on bringing Office 365/Microsoft 365 inline with best practice
If you use third party mail filtering, you can get Exchange Online to do a secondary check by enabling Enhanced Filtering. Ain't nothing wrong with a second opinion when it comes to phishing
Sometimes there is no exciting guidance, you just need to update your old stuff!
Guidance to secure privileged accounts, including seperation of on-premises admin accounts from cloud admin accounts, removal of mailboxes from admin accounts and separate admin accounts from regular day to day accounts
The section of the Microsoft Azure Well-Architected Framework that covers administrative account security
Understanding why privileged access devices are important and where they fit on your privileged management journey
The Microsoft Enterprise Access Model guidance, this model seeks to reduce the spread of privileged credentials and paths to privileged accounts by securing tier 0 assets and users
Lists all the various locations to configure guest settings including Entra, SharePoint, OneDrive and Teams
Microsoft Learn documentation on protecting data with Microsoft Purview including information labels, insider risk and data compliance
Microsoft Defender now has vulnerabilty management capability which you can see within the M365 Defender Portal
You can integrate vulnerability management into Microsoft Defender for Cloud, this includes both virtual machines and vulnerability analysis for containers and other cloud native products
A list of tasks that can be completed in Microsoft Entra ID and the role that allows a user to complete that action while adhering to least privilege
Implementing least privilege administrative models in on-premises Active Directory