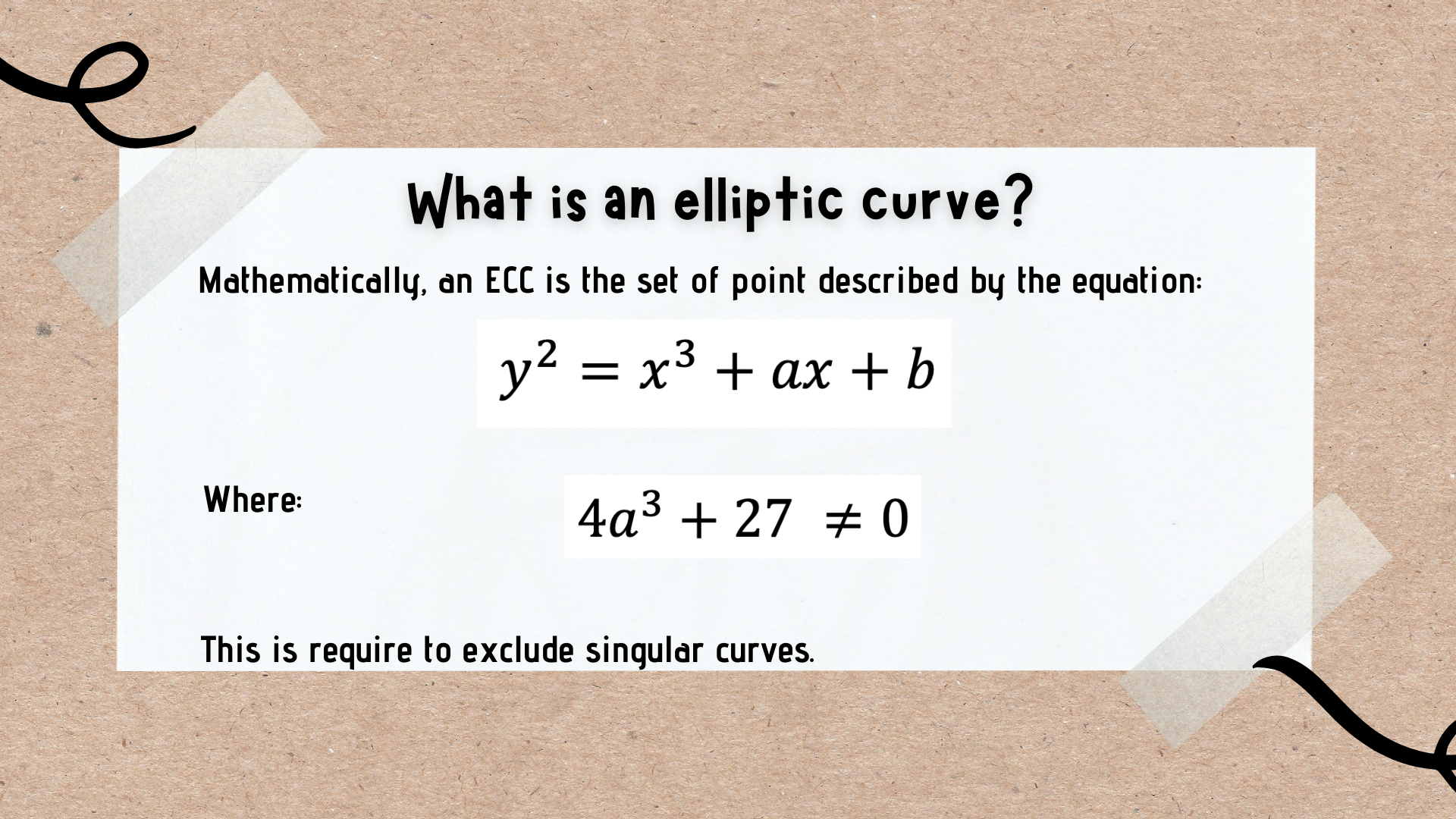Today we are going to learn about a bit complex topic Elliptic Curve Cryptography (ECC), to provide a simple overview of what ECC is and why it is considered secure.
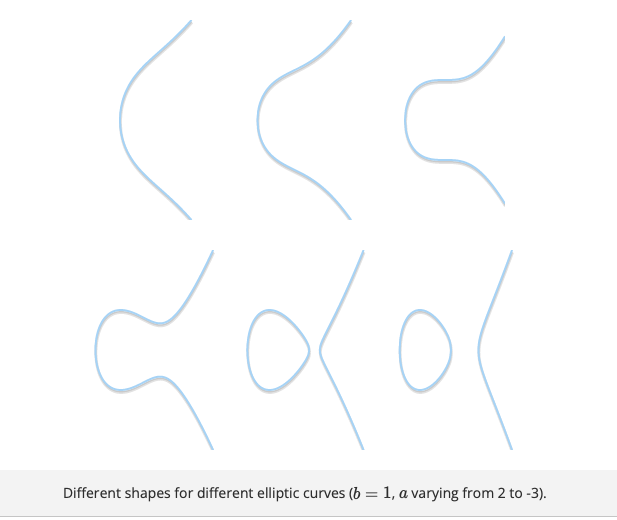
The equation above is what is called Weierstrass normal form for elliptic curves. Depending on the value of
We will also need a point at infinity (also known as ideal point) to be part of our curve and denote with the symbol 0 (zero).
In order for the set
That's all for this thread. Thank you for reading! If you liked this thread, follow me @Hasseru and retweet.
Corbellini, Andrea. Elliptic Curve Cryptography: a gentle introduction.